April 2018 | Point of View
Cybersecurity for utilities: Protecting the new digital landscape
Learn the cybersecurity threats appearing from the new digital landscape and how to take an approach that secures a utility’s communication infrastructure
As utilities move forward with modernizing and upgrading their operational technology (OT) networks, the progression toward converging them with information technology (IT) networks increases. While the benefits of integrating a utility’s IT and OT networks under a single operational umbrella are demonstrated, rising security threats and evolving security and privacy requirements come into play.
Individual attacks and cyber warfare tactics highlight the importance of critical infrastructure investments that will strengthen information security, build resiliency into operations, and encourage IT and OT collaboration in a technology-driven environment. Adding to the pressure is intense scrutiny from regulators and customers on the security, safety, and operational reliability of power delivery, as well as an unprecedented array of regulatory requirements, such as the North American Energy Reliability Corporation’s (NERC) Critical Infrastructure Protection (CIP) standards.
While many of the requirements and regulatory factors are directed to the electrical industry, the same principles and best practices can also be applied to water, oil and gas, and to the new Internet of Things (IoT) digital arena.
Chapter 1: Industry executives cite cybersecurity as top concern
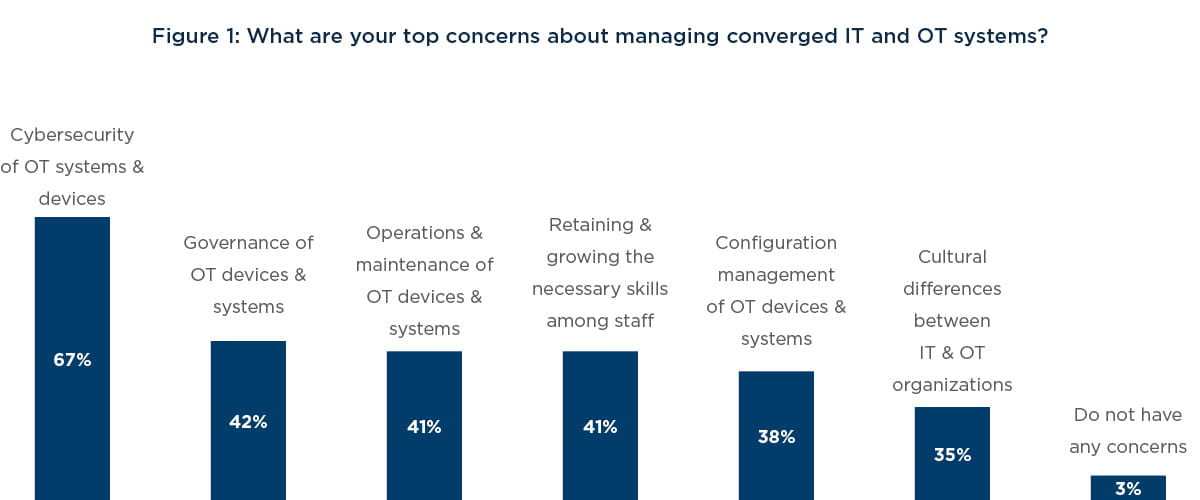
In a recent West Monroe survey, 67% of utility leaders cited cybersecurity as their top concern of their converged IT and OT network.
While cybersecurity of the electrical grid is top-of-mind for most, the systems maturity, policies, and governance of security models are lacking. More concerning is the disconnect between C-suite executives and those on the front lines tasked with providing the necessary protection and execution of the organization’s security plan and posture. While executives believe the proper tools and processes are in place to prevent a breach, technical officers have a more pessimistic view of their own environments and capabilities.
According to a recent report, “Cyber Threat and Vulnerability Analysis of the U.S. Electric Sector” from The Department of Energy’s Idaho National Laboratory, they have also called for renewed awareness about grid security and further identify the risks and concerns of those charged with protecting the reliability of power delivery: “The potential for malicious actors to access and adversely affect physical electricity assets of U.S. electricity generation, transmission, or distribution systems via cyber means is a primary concern for utilities,” the researchers wrote.
This possibility was exploited and widely reported in late 2015, when a Ukrainian utility was remotely hacked and impacted power delivery to 225,000 people in the country. According to a detailed study of the incident by the Electricity Information Sharing and Analysis Center, it was “the first time the world has seen this type of attack against OT systems in a nation’s critical infrastructure.”
Chapter 2: Is the United States’ critical infrastructure vulnerable?
While there have been no successful cyber-attacks against U.S. utilities that caused permanent or long- term damage to power system operations, researchers cautioned there has been “a steady rise in cyber and physical security-related events.”
A 2017 article in Wired Magazine stated Symantec revealed a new offensive of attacks that targeted dozens of energy companies. In more than 20 cases, Symantec says the hackers successfully gained access to the target companies’ networks. And at a handful of U.S. power firms, their forensic analysis found that hackers obtained what they call “operational access”—control of the interfaces that power company engineers use to send actual commands to equipment like circuit breakers and reclosers. This gave the intruders hands-on remote access and the ability to stop the flow of electricity into homes and businesses, and could have induced blackouts across America.
With this real threat, and increasing digitization, interconnectivity, and automation of our energy infrastructure, electrical grid operators must continue to provide cyber-resilient energy delivery systems. The attack surface of a utility’s infrastructure continues to expand as intelligent distribution systems, sensors, and IoT devices aid in the visibility of the electrical system and assist with ensuring power delivery in the most efficient and reliable manner. With this expansion comes a greater need to ensure security is properly implemented, end-to-end.
The electrical grid faces a multitude of threats and vulnerabilities (physical attack, electromagnetic pulse, geomagnetic storm, solar flares, inclement weather, etc.), as well as cyber-attacks from multiple nation states and outside actors. The inefficiencies, from being able to quickly correlate and analyze the insurmountable digital events from multiple sources to the lack of internal communication between network and security operation centers, can result in missing a breach or stolen credentials to shut down critical components of the electrical grid.
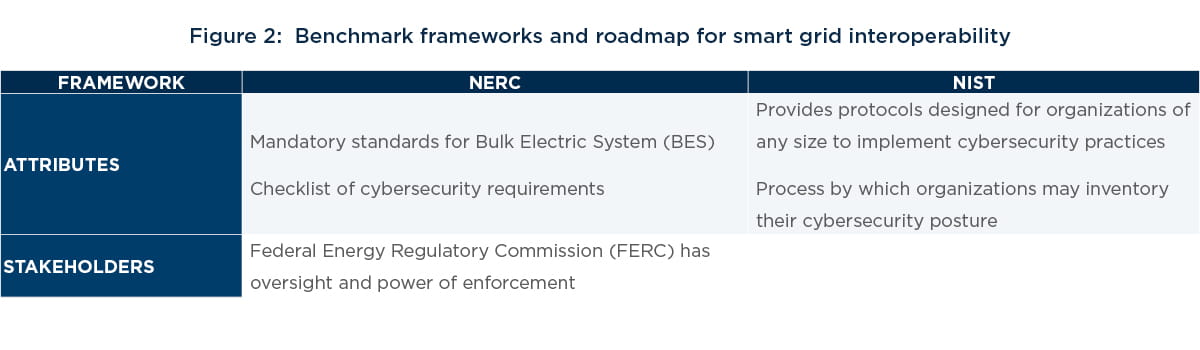
Chapter 3: Industry frameworks are a good place to start
A variety of federal and state cybersecurity regulations and recommendations exist to guide U.S. utilities on how best to incorporate cybersecurity into general risk management practices.
While mandatory requirements protect assets critical to energy transmission, such as those of the U.S. BES, some industry leaders, including our own Director of Security, Sean Curran, worry that “standards can lead to a focus on compliance at the expense of an overarching cybersecurity strategy,” perhaps even impeding practical cybersecurity measures.
Many of these frameworks provide a baseline to measure security effectiveness and meet compliance requirements. But there is often a lack of skilled resources, talent, and knowledge to address the challenges of an in- depth security approach. Many utilities ask, “Where do I start?” For many, the answer lies in ensuring the fundamentals of a cybersecurity program are well laid-out, prioritized, and planned for.
Chapter 4: 3 steps utilities can take now to improve security
Step 1: Assess your risk portfolio
One of the first steps a utility can take to toward launching a successful, defense-in-depth, risk-based security strategy is to complete an organizational study. This would involve building a cybersecurity plan to identify critical assets and prioritize the risk they would impose if compromised or lost.
This ongoing process of identifying, assessing, and mitigating risk is critical component to operational resiliency. Utility organizations must understand the likelihood of an event and the resulting impact it would have to reliably deliver power. With this information, utility organizations can determine the acceptable level of risk for delivery of services and can express this as their risk tolerance. With an understanding of risk tolerance, these organizations can prioritize cybersecurity activities, enabling utility executives to make more informed decisions about cybersecurity expenditures.
This comprehensive view of a utility’s current level of prevention helps identify gaps and gives organizations the ability to dynamically select and direct improvement in cybersecurity risk management for digital utility environments.
Step 2: Pervasive security architecture
As new systems and devices are constantly added to improve the performance, resiliency, and restoration of the grid, a holistic security architecture and design process should be addressed and integrated from the ground up, and not just bolted on after the fact.
Historically, communication infrastructures were put in place before security was even thought of or regulated. With the advent of IoT, the edge of the network continues to grow and expand. Issues and vulnerabilities, like the Mirai botnet malware—which led to wireless cameras and unsecure routers to create a DDoS attack on specific Internet backbone providers that resulted in outages— continue to be exploited and recoded for other purposes. Securing and protecting the grid from the ever-increasing number of sensors and devices will become paramount to ensure grid stability. Identification of assets, proper access control, and data flow segregation will all be crucial services that will need to be designed and architected as the edge of the network continues to grow and expand.
Step 3: Utilize common security tools
Firewalls and trust zones: Network firewalls are one of the first lines of defense utilities use in their security architectures to protect IT and OT systems from malicious cyber activity. Firewalls must continue to block external threats and must now be configured to block and control traffic to distinct internal zones of the network and separate the network into distinct “trust” zones. Boundaries for these trust zones are particularly important for utility networks that combine IT and OT systems. Non-existent or easily penetrated internal firewall boundaries allow a potential hacker easy access to any part of a utility’s assets.
Most firewalls now use a capability called deep packet inspection (DPI) to inspect network traffic traveling to and from control and automated systems and blocking inappropriate traffic. DPI firewalls apply more detailed inspection to network traffic, rather than simply implementing a traditional black/white list method.
More specifically, DPI firewalls can be used to separate malicious data messages from benign ones. This is particularly useful in SCADA systems where malicious data messages need to be differentiated from routine control messages.
Anti-virus application and control software: Like other cybersecurity-conscious businesses, most utilities implement some sort of antivirus software on networked computers to prevent traditional malicious cyber-attacks. One alternative to traditional antivirus software is the use of secure application control software, if supported in an industrial control system environment. Application control software allows for a variety of trusted applications to run in a critical infrastructure system.
All other higher-risk or dangerous applications are simply blocked and not allowed to be executed in the system. This contrasts with simply blacklisting known threats and allowing unknowns. In addition to increasing cybersecurity, utilities have found that some types of application control software can also reduce the number of required patching cycles and maintain regulatory security standards for utility systems.
Encryption of intelligent device communication: Another frequent practice many utilities have adopted is data encryption, particularly encryption of communication data. Encryption has long been used in IT systems to prevent undesirable third parties from intercepting and reading data messages. Some utilities currently use encryption software to encrypt SCADA communications to prevent hackers from collecting information on control processes for the electric grid.
Encryption is particularly important to utilities to protect the privacy of smart meter communication data. The emergence of smart grid metering technology in North America and around the world has made encryption of communication data an even higher priority for electric utilities. To ensure proper encryption, cryptographic protocols are already being developed, such as the standard put out by Institute of Electrical and Electronics Engineers, to encrypt information transmitted from utility substations.
User rights and access control: Additional areas that must be accounted for and improved upon are the Authentication, Administration, and Accounting (AAA) practices by ensuring resources have the proper rights and credentials, all data flows are properly analyzed and understood, and anomalies are reported and tracked.
Most of the reported breaches started with a phishing email attack that someone inside the utility clicked on, or a USB stick was compromised, connected to a laptop, and unknowingly installed malware on their computer system that opened the door to further exploits and intrusion.
This compromised inside actor allowed for further exploration around the network and the ability for the malware to be spread to potential control devices inside the utility.
By baselining proper network traffic and using these as points of context, a security operator within the utility can identify suspicious activity, gather pertinent user information, and then assess and respond to the potential danger of the suspicious activity or unusual traffic pattern. From there, the operator can formulate and execute remediation for affected users and/or systems.
Security systems must have the ability to provide complete insight to the history and status of the user, policy, posture, and device, as well as quarantine or network disconnect remediation functions. Collectively, these context and remediation capabilities enable a utility operator to decipher the correct next steps to address the threat in a timely, efficient, and cost-effective manner. Having real-time analysis engines to identify proper traffic patterns and data flows (and quickly report on unusual activity), as well as role-based authentication rights and permissions for users and operators, are critical to the defense-in-depth strategy.
Conclusion: Securing the grid to keep the lights on
The recommendations mentioned above are good first steps to apply a comprehensive, risk-based security approach. They also provide a detailed look at how the resources of an organization are structured so that grid security can be addressed in a manner that balances protection with the need to provide affordable energy to consumers. Prioritization and proper planning are key to ensuring further collaboration, communication, and understanding to maintain a resilient and reliable power grid within an electrical utility.
Outside bad actors and forces won’t stop trying to infiltrate and breach our utility infrastructures and control devices. But with the proper systems, tools, detection, isolation and remediation plans, we can ensure that power delivery remains stable and the lights stay on.